Signed in as:
filler@godaddy.com
Signed in as:
filler@godaddy.com
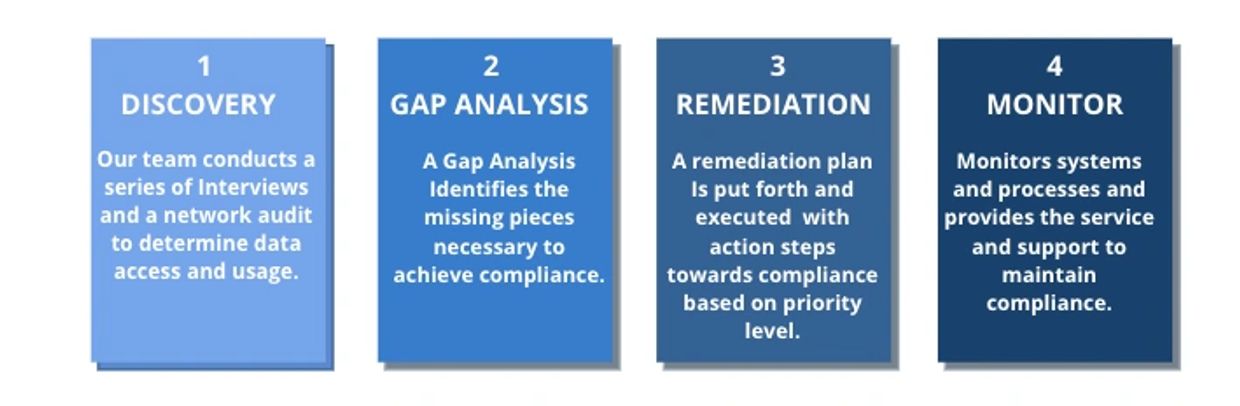
Ready for CMMC? No? You might think that delays in the deployment of CMMC for DoD contractors means it isn't coming, but can you be sure? Assessing your NIST SP 800-171 compliance is only part of achieving certification - we provide a 3 to 7 day discovery assessment of your environment that includes a high-level, prioritized gap analysis. We'll also help you build a Plan of Action & Milestones so you'll know what you need before CMMC becomes a reality!

In 2015, the Department of Defense (DoD) published the Defense Federal Acquisition Regulation Supplement (DFARS) to push private contractors to maintain cybersecurity standards according to the requirements the National Institute of Standards and Technology (NIST) outlined in NIST SP 800-171.
Created to ensure the protection of Confidential Unclassified Information (CUI), the standards outlined in DFARS and NIST 800-171 gave DoD contractors until December 31, 2017 to meet the requirements necessary to be compliant or risk losing DoD contracts.
To be classified as compliant, contractors merely had to attest to meeting the requirements or being in the process of satisfying them.
As a result, U.S. adversaries have been able to develop military equipment based on stolen data. For instance, the Chinese J-20 and J-31 stealth fighter jets suspiciously resemble the American F-35. According to the Pentagon, China may have accessed the F-35 design after an information breach in 2009.

The Cybersecurity Maturity Model Certification (CMMC) is a new certification model designed to verify that DoD contractors have sufficient controls to safeguard sensitive data, including Federal Contract Information (FCI) and Confidential Unclassified Information (CUI) .
The CMMC model uses the basic safeguarding requirements for FCI as the Federal Acquisition Regulation (FAR) Clause 52.204-21 and the security requirements for CUI as specified in NIST 800-171 / DFARS.

Examples of CUI:

The CMMC acknowledges that not all information shares the same levels of sensitivity, and not all contact participants have the same clearance levels. Because of this, the Cybersecurity Maturity Model Certification measures processes and practices across five maturity levels.
The achievement of higher CMMC levels enhances the ability of an organization to protect CUI. For Levels 4-5, it also reduces the risk of advanced persistent threats (APTs), which are often executed via multiple incursions, including cyber, physical, and deception.
There will be five cumulative Certification levels to the CMMC:
Level 1 – Basic Cyber Hygiene: Includes basic cybersecurity appropriate for small companies utilizing a subset of universally accepted common practices. The processes at this level would include some performed practices, at least in an ad hoc manner. This level has 17 security practices that must be successfully implemented.
Level 2 – Intermediate Cyber Hygiene: Includes universally accepted cybersecurity best practices. Practices at this level would be documented, and access to CUI data will require multi-factor authentication. This level includes an additional 55 security practices beyond that of Level 1.
Level 3 – Good Cyber Hygiene: Includes coverage of all NIST SP 800-171 Rev. 1 controls and additional practices beyond the scope of current CUI protection. Processes at this level are maintained and followed, and there is a comprehensive knowledge of cyber assets. This level requires an additional 58 security practices beyond those covered in Levels 1 and 2.
Level 4 – Proactive: Includes advanced and sophisticated cybersecurity practices. The processes at this level are periodically reviewed, properly resourced, and are improved regularly across the enterprise. In addition, the defensive responses operate at machine speed and there is a comprehensive knowledge of all cyber assets. This level has an additional 26 security practices beyond the first three levels.
Level 5 – Advanced / Progressive: Includes highly advanced cybersecurity practices. The processes involved at this level include continuous improvement across the enterprise and defensive responses performed at machine speed. This level requires an additional 15 controls security practices beyond the first four levels.

A landmark effort by the Department of Defense to shore up cybersecurity across its 300,000+ contractor base has managed to stay mostly on schedule despite the coronavirus pandemic.

Currently, non-compliance can result in criminal and civil litigation, along with fines and other penalties being levied against the business. If CUI is breached and the contractor is found to be out-of-compliance, it can result in the termination of the contract and the company is restricted from bidding on additional projects.
Some of the other penalties that businesses could face include,
IQ CMMC Services (pdf)
DownloadCopyright © 2021 Viqtory Cyber - All Rights Reserved.